Attaining a ‘single customer view’ is perhaps the primary objective for every digitally focused business. If you can understand who is browsing and buying, where they are doing it, when they are doing it and why they are doing it then the ability to communicate with these people in the way they will expect will be possible. There are however many blockers, restrictions and caveats with attaining this view. In this article we will attempt to get to the bottom of which methods could be used to generate and manage a customer identifier (primary key) and their implications and usage options.
What sort of business are you?
This might seem like a very basic question to ask yourself but it is an extremely fundamental one. The main points to establish here are these:
- METHOD: Can you identify a significant proportion of your users in a unique and accurate manner?
- USAGE: If you could, would you actually be using the data to influence their experience?
Depending on what sort of business you are, your approaches to setting customer identification keys is likely to be very different.
Methods
While there are many ways to set an identification key they will broadly fall into two sub-categories:
- Authenticated
- Inferred
An authentication method relies on a being able to ascertain a piece of personally identifiable information (PII) from the customer. Before you start getting concerned about various EC Directives around PII let’s not forget that PII can be encrypted such that it can still be used as a key but not allow any malicious individuals or software to benefit from knowing the encrypted value. PII will also have to be provided directly by the customer and will often be required for a site/app to function. As long as the customer is aware of what this data is being used for and agrees to this there should be no conflict of data privacy laws.
Examples of businesses that are likely to be able to benefit from this method include those with a subscription model, financial institutions, ecommerce sites/apps, community services and pretty much any other business that has a product or service that is not available entirely for free.
An inferred method relies on cookies and/or other behavioural triggers to deduce whether a customer key should be used. This too has the same considerations to be made around PII and as such, any key used for the purpose of understanding combined behaviour should be encrypted to avoid any additional data privacy pitfalls. Depending on the market you operate in you may also require formal consent to use this data.
Businesses needing to use the inference method will ultimately be any business that does not mandate personal data capture at any stage. Examples may include media publications or content aggregators and other businesses that rely purely on advertising revenue.
In our experience, many of the companies we work with would actually fall into both camps. There will be many instances of activity on a site or in an app that does not require data capture (browsing) with a subset of activity requiring data capture (purchasing or accessing account preferences). There are options for all companies to achieve some degree of a single customer view. Caveats and limits will exist based on the type of business they are but we also find that actually the bigger barrier is the confidence and collaboration across the business required to start making use of the methods available.
Usage
So, you’ve figured out what sort of business you are and whether you can operate an authentication, inference method or have to use a combination… great. The next major hurdle is to decide what you’re going to do with this data when you have it. Do you want to collate data simply for the purpose of delivering management information dashboards or do you want to use this data to alter the user experience in real-time based on what you know about them?
The way I like to think about this is to ask a simple question: How will the business change if we know more about our customers?
If the answer is ‘it won’t’ then I have a harsh point to make for you… stop reading this document and carry on with your current analytics and reporting methods. There will be no point in investing time and money into something that does not get used inside the business to affect positive change.
So, what form could this positive change come in? Let’s imagine a few scenarios:
- Ecommerce Site
- Retargeting – instead of showing relatively generic retargeting ads based on what product I have looked at but purchased somewhere else, we could use the combination of 1st and 3rd party data to find other related products or even complimentary products to push.
- Example – customer goes on to an outdoor pursuit’s site and looks at 3 tents but does not add any to their cart. We know they are interested in tents but may have already bought a tent elsewhere by the time we reach them. We also know the customer have an interest in festivals and live music from our 3rd party data. We also know that other customers who have bought tents have commonly bought accessories such as stoves and chairs. Why don’t we retarget them by offering a ‘festival pack’ which includes a discount when buying camping accessories that would be useful to take to live events?
- Publishing Site
- On-Site Personalisation – most publishing sites have a ‘most read’ or ‘trending’ section to promote stories that are experiencing high volumes of traffic that day or perhaps within the last hour or less. However, why don’t we use the data we have about a specific customer’s behaviour to influence this list and personalise it to what they are interested in.
- Example – customer returns to a news broadcast site. With our first party data we know that this customer favours lifestyle stories and sport over political or current affairs for example. Instead of show them a ‘most read’ module let’s show them a ‘for you’ section as well as a generic ‘most read’ module.
- Brick & Mortar Business
- Geo-Location Targeting – let’s assume this business also has a website and an app. The customer has signed up to receive offers and promotions and they have a loyalty card that they use in store. In this case we’ll actually be able to know where they are and potentially what offer might incite them to buy.
- Example – the customer has a buying pattern that suggests they make fewer large purchases as well as a more frequent number of top-up purchases (for bread and milk etc.). We can detect their proximity to a ‘local’ store and therefore based on when their last large purchase was can deduce they may be interested in a top-up purchase. What we can now do is provide a personalised offer for them on a product that we’d like them to try out. The idea here being that if we can get them to try a new product it may start to feature in their large shops as a regular item if they like it.
If all you want to do is create a shiny report that shows overlapping of behaviour across devices/channels for example then invest in a decent one-off survey each year and you’re done. If however the ultimate goal is to use this data to drive change within the business and improve the customer experience then read on.
Implementation
Now that you’ve established what method(s) are available to you and that you want to use this data to do more than reporting, we can think about the implementation options. As far as we see them they are:
- Authenticated
- Direct
- Indirect
- Inferred
- Cookies
- Behaviour
Authenticated: Direct
This requires a physical action to occur from the customer. The action will include passing across some PII which will be sent off to a system using a secure httpss request which will in turn read this data and pass back an encrypted customer key that is consistent against the customer’s PII. Example actions where this may occur could be a newsletter sign up, quote request, account sign up, service log in, purchase and so on.
Authenticated: Indirect
This method is still reliant on the direct authentication method. The difference here is that instead of requiring a physical action to occur to use the customer identifier it stores the customer identifier in a cookie after an initial direct authentication. This cookie will have specific expiration rules such as time-based or event-based. For example, the typical flow where this might be used is:
- Day 1 = Browse & Register (Direct Authentication)
- Day 2 = Return to site (Indirect Authentication)
- Day 3 = Return to site and log out (Indirect Authentication cookie expired)
- Day 2 = Return to site (Indirect Authentication)
Inferred: Cookies
This method will only be as reliable as your customer’s dependence on their specific device and browser combination as well as their desire (or lack thereof) to block cookies. That being said it is still possible to track a significant amount of behaviour this way to give pockets of insight about what the customer is doing.
For example, when a customer arrives at a site that does not require any form of authentication we’re unlikely to ever really know who they are. However it is entirely possible to confidently infer attributes about them using a combination of 1st and 3rd party data. 1st party data would be being built up via a tracking system that collates data directly owned by the business using a 1st party cookie. Such data could include what products they have looked at, items they have added to the cart or the fact that they have not purchased this item yet.
3rd party data would be being built up via a tracking system that collates data that could be utilised (not owned) by using a 3rd party cookie to store data against a specific domain. For example one such domain would be ‘doubleclick.net’. As part of an advertising partnership it would be possible to utilise this 3rd party data to enrich 1st party data to build a single view of the customer. For example, it may be possible to know via this data enrichment more about the customer’s personal interests or preferences based on other sites and other types of content and/or products they had been looking at.
If you’ve ever used or investigated the potential of using Google Analytics and AdWords to create a retargeting campaign you can see this enrichment working in harmony. Google will utilise data recorded directly by the analytics system (1st party data) and enrich it with additional demographic data (3rd party data) for the purpose of finding audiences to specifically retarget advertising campaigns to. For example:
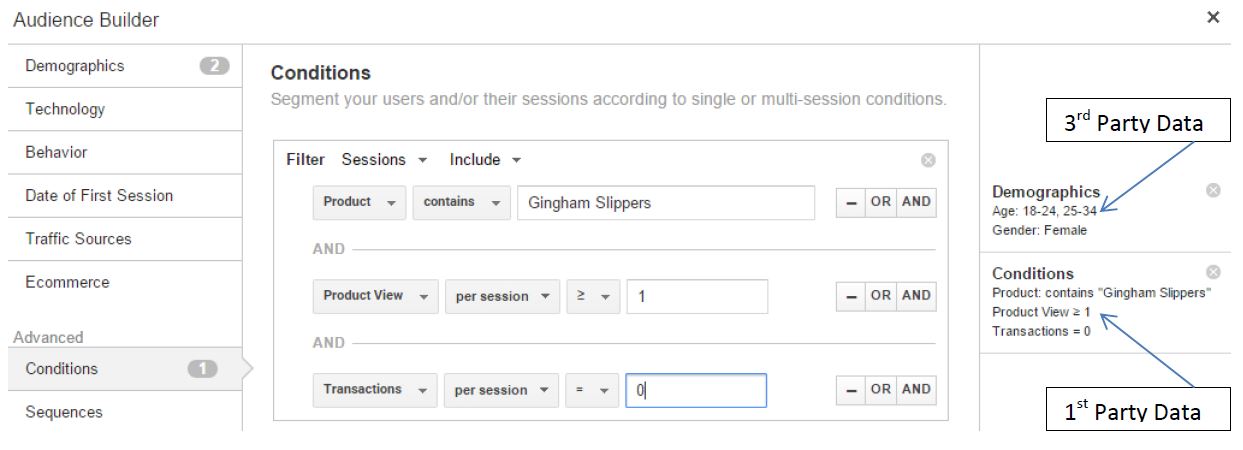
NOTE – there are two ways a cookie can be set which play a very significant role for any company looking to adopt an inferred method of identification:
- JavaScript
- HTTP/S Request
The JavaScript method is by far the simplest way of setting a cookie and will often feature as a default method for understanding ‘Unique Visitors’ by analytics systems such as Google Analytics or Adobe Analytics. It works by a script executing logic directly in the browser to set and store a unique value for a customer. It can only set a cookie against the domain the user is on. This can be set at the sub-domain, domain or domain and directory level but cannot be read/used by any other domain.
The HTTP request method involves an initial communication with a tracking server. A request is originally sent to this tracking server and if no cookie is present then the tracking server will respond with a 302 redirect request to itself and generate a cookie ID to be stored by the browser before the request comes back to the server. From this point onwards if the customer does not delete their cookie there will be no need to re-request the cookie ID from the tracking server. The additional benefit this has over the JavaScript method is as follows:
- Avoids any potential client-side execution issues (perhaps from obscure plugins)
- Allows data to be set against a different domain to the one the user is on
The advertising industry by enlarge uses https/s cookies over JavaScript cookies for the simple reason that they can be set against an independent tracking domain allowing them to retain data between different domains the customer accesses. This is what allows the data enrichment in the Google Analytics Remarketing example above.
Inferred: Behaviour
Inferring relationships in data based on specific behavioural attributes is not a simple task. It involves using or building a service that can interpret a lot of different data points and create an accuracy propensity model to determine whether behavioural patterns are similar enough to combine data together.
For example, the rules may be looking at a combination of IP address, devices, timestamps, interests and possibly indirect authentication data such as click-throughs on email. While much of the data will be stored against a cookie building up data the actual processing of this data will occur on a server (or in the ‘cloud’) by finding patterns in what would otherwise be disparate data. Based on a tolerable level of statistical confidence (80+% ?) the data will then be automatically merged for the purpose of presenting a combined view of a customer’s behaviour across browsers and/or devices.
Putting This All Together
So, we’ve covered the basic principles of how you could set a customer identifier but how do you put it all into practice? Well, in my opinion it all hinges off the purpose of doing this. If you are clear as to how you will use the data you have for your customers if you can attain it, then this and the combination of what data options are available to you will define how it comes together.
To take an example – a relatively complex one – that is fresh in my mind I will use a scenario for a news broadcasting business that has little access to authentication data, but does have good 1st party data via their analytics and access to a Data Management Platform (DMP).
Method:
- Establish a single cookie ID service that operates across their primary domain
- This will manage cookie generation using https requests
- Share cookie ID with their User ID service
- The User ID service is used where authentication is possible creating an automatic bind between pre and post-authentication
- Use DMP to enrich 1st party data
- This will allow data captured when the customer was one other sites to enrich the 1st party on-site behavioural data
Usage:
- 1st Party Data – My activity on the site in the last 24 hours suggests a preference for technology news
- 3rd Party Data – I’m known to have accessed sites like techradar.com and wired.co.uk in the last 7 days
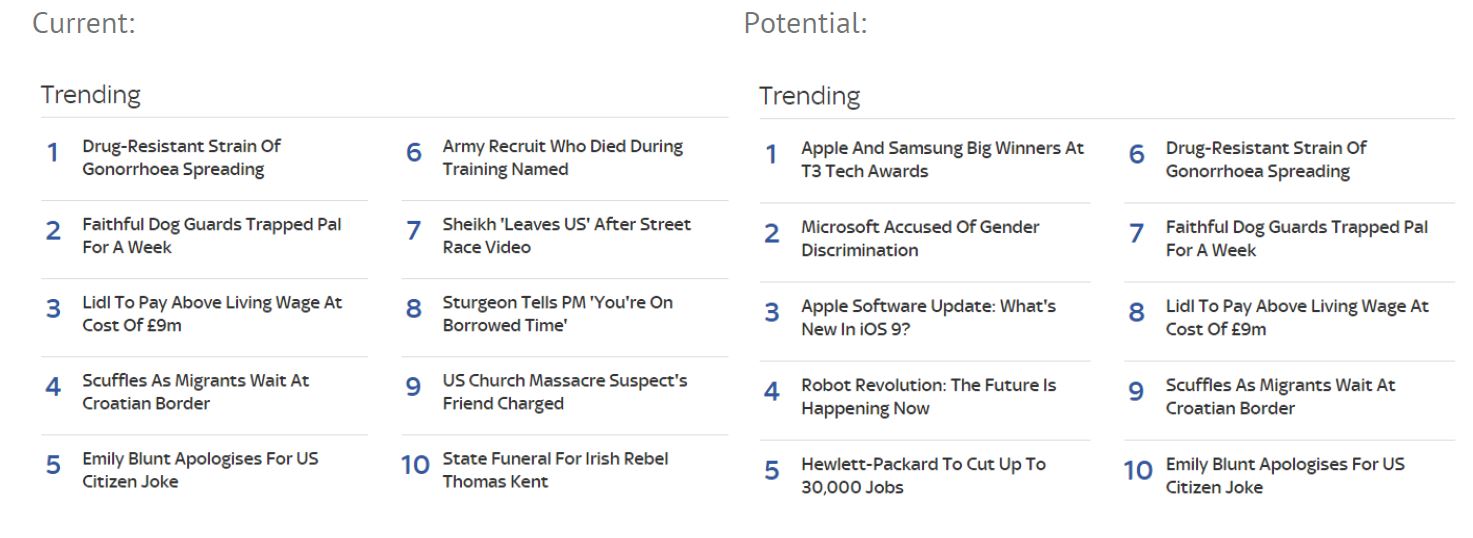
In the above example this particular news site has a generic ‘trending’ section presented on all category pages to customers. The example next to it will alter content based on the customer falling into different targeting segments. In this case as the 1st and 3rd party data suggests I’m trying to discover more technology related news the first 5 articles here are the technology trending articles with the second 5 being across all categories.
If the customer were to then sign up for newsletters we could automatically entice them with fresh technology content given the automatic join in IDs prior to providing their email address…
If you need some help thinking through how you should be managing your customer identifiers and the implications this will have both on your data, but also how that data can be integrated into other tools that can affect the customer’s experience, then please get in touch with us to discuss it further.


Leave A Comment
You must be logged in to post a comment.